How Good Cybersecurity Strategies Are Shaped by Threat Intelligence Research
“The importance of epistemic security and cybersecurity is now comparable to that of national security.”
– Roger Spitz (Futurist)
Cybersecurity is among the top priorities for nearly every business in this world and the increasing number and complexity of cyber threats is undoubtedly a matter of concern and a wake-up call for them.
It is a sign for companies to put thorough security measures for protecting networks, systems, and sensitive data into action.
Currently, threat intelligence research is one of the most effective strategies available to keep systems ahead of cyberattacks. According to reports, businesses with threat intelligence are 78% more likely to detect and prevent breaches early on. (LinkedIn: Real-Time Threat Intelligence)
Curious to learn more? In this post, we will discuss how threat intelligence is reshaping cybersecurity. So, stay tuned to learn how it can help companies identify, stop, and handle potential attacks.
Define threat intelligence
It is essential to understand threat intelligence before we discuss its role in cybersecurity. Threat intelligence—knowledge about possible or ongoing attacks—is applied to navigate a company’s action plans. Threat detection is simply the process of gathering data from different sources—internal and external—analyzing it and then utilizing its outcomes to guide cybersecurity decisions.
Threat intelligence helps them create attack routes and define tactics, strategies, and procedures (TTPs), integrating Command, Control, and Execution. It enables firms to gain insight into the threat landscape to stay ahead and can start from your systems, outside sources, open-source information (OSINT), or commercial threat feeds.
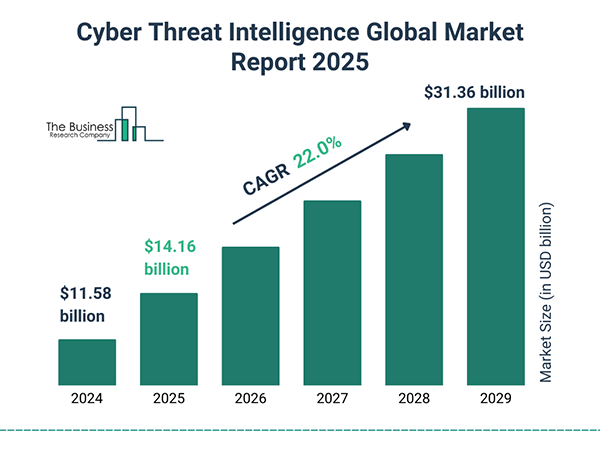
With increasing risks, the cyber threat intelligence market is on the rise and is projected to reach $32.36 billion by 2029.
Threat Intelligence’s Importance in Cybersecurity
Threat intelligence plays an important part in shaping effective cybersecurity plans. This affects essential spheres as follows:
Proactive Defense Mechanisms
Cybercriminals are constantly advancing and adapting their strategies to bypass traditional security measures. Threat intelligence allows organizations to stay ahead of cyber threats by detecting trends and emerging risks before they escalate.
Studying prior attacks allows businesses to put active defensive systems in place, knowing the strategies attackers employ.
For instance, cybersecurity teams can stay prepared by bolstering defenses in sectors likely to be targeted if threat intelligence identifies a fresh ransomware strain aimed at a given industry. Through this proactive approach, companies can stop attacks before they even start.
Enhanced Reaction to Incidents
It is extremely important to quickly grasp what kind of threat you are facing during an attack and this incident response depends heavily on real-time information. Threat information provides the attack background for the incident response teams that may contain and swiftly repair harm.
The cybersecurity reaction team can respond more effectively, understanding the kind of attack, the tools the attackers employed, and the attackers’ likely intentions.
For example, threat intelligence, in case of data breaches, will provide the latest methods used to target a weakness. This lets the security team resolve the issue from the source and ensure it won’t be repeated.
Improving threat detection
A robust threat intelligence program leads to better decision-making, an enhanced security posture, and proactive risk management, allowing organizations to respond to emerging threats faster and more effectively. With increased knowledge of attack patterns, security systems can adjust to find specific indicators of compromise (IOCs). Unusual network traffic and odd file activity could indicate an assault that is either already underway or fast approaching.
This approach allows companies to include intelligence in their security operations and create smart systems that are capable of monitoring hazards 24/7. Firewalls and intrusion detection systems, for example, can flag any unusual activity with the help of threat intelligence data enabling your security teams to respond immediately.
Giving Safety Efforts Top Priority
The dangers associated with every threat are not on equal levels, and cybersecurity resources are limited. Giving security efforts top priority threat intelligence makes the first component of a convincing security response, as it helps identify the most imminent risks to the organization.
Instead of offering security, let businesses improve their priorities in safeguarding their systems and combating the vulnerability with the highest risk based on intelligence data.
For example, if according to threat intelligence, there is an increase in attacks aimed at a particular vulnerability your company owns, your top priority should be fixing that vulnerability. This narrows the total assault surface and promotes effective resource use.
You are now reading a threat intelligence research article.
Investing in threat intelligence research can help companies with various aspects:
Alert Indices of Emerging Concerns
The main feature of threat intelligence is that it can assist in finding new hazards before they develop. Staying on top of the threat scene and knowing new attack strategies allows companies to proactively modify their cybersecurity systems, significantly decreasing the possibility of being caught off guard.
It can also reveal new and unexpected attack routes, such as the rise of undercover phishing campaigns or zero-day exploits, strengthening the company’s defenses before the threat is fully apparent.
More team cooperation
Threat intelligence encourages improved cooperation among other business units, its staff, and security teams. Also, higher cooperation among security teams, IT personnel, and other company departments is promoted by it, sharing ideas across several departments assists in building a more coherent cybersecurity plan.
Threat intelligence can recognize various kinds of problems, say a vulnerability in a software product, which may require the security team to track for exploitation of this issue or the IT department to update the software.
Improved Decision-Making
Accurate, timely data lets companies allocate their cybersecurity funds more wisely. Threat intelligence consistently delivers information needed to make better decisions, such as which security technologies should be used or where to channel funds in the detection systems.
Having the knowledge of the present threat environment helps one make more business-relevant judgments about security policies, enhancing general security posture.
Threat Intelligence Sources
Good threat intelligence is based on multiple facts from many different sources. These sources provide the necessary knowledge to help spot and manage risks. Here are a few often occurring forms of sources:
1. Internal Threat Intelligence
Internal threat intelligence is a manifestation of systems within a company. This can include logs, network traffic data, and any other output generated by the company’s network architecture. By analyzing the internal data, companies can find odd behavior suggesting a possible assault.
For instance, tracking illegal access attempts or unusual outgoing traffic can assist in finding harmful movements within the network.
2. External Threat Intelligence
As the name suggests, intelligence regarding external threats comes from outside a company. This usually covers industry groupings, government agencies, and commercial vendor intelligence.
Many companies spend on intelligence programs offering current data on vulnerabilities, new risks, and attack patterns.
This keeps companies up-to-date about hazards that might not directly impact them at the moment but could cause danger in the future.
3. Open Source Intelligence (OSINT)
Open-source intelligence is the data available publicly that can be utilized to spot cyberattacks. Usually composed of information from blogs, forums, social media, and other publicly available sources, this helps track conversations regarding developing risks or vulnerabilities, organizations can use OSINT to avoid cyberattacks.
4. Intelligence on the Dark Web
The dark web is another significant source of dangerous intelligence. Cybercriminals often share data, hacking tools, and exploits, on the dark web. Constantly surveying dark web traffic helps companies understand the hazards and illicit behavior that might impact them.
For instance, in case a company’s data shows up for sale on the dark web, a quick reaction can help minimize further damage.
DO YOU KNOW?
Threat intelligence is often described by the “Three Ps” – Proactive, Predictive, and Preemptive, meaning it aims to anticipate threats before they occur and take preventative measures.
Using threat intelligence, get ahead of cyber dangers.
With constantly evolving cyber threats, staying ahead means keeping an eye on and adjusting to fresh hazards as they arise. Regular research on threat intelligence guarantees that fresh data involving attack strategies, tools, and patterns fuels this process.
Companies may leverage threat information to stay ahead in the following ways:
- Establish systems to automatically see and handle threat intelligence data with the help of the Automated Threat Intelligence Framework. This involves forming a division to monitor the threat environment and send threat data into security instruments.
- Utilize tools that compile and compare threat data from different sources using intelligence platforms. However, having access to these facilitates community sharing via tools designed primarily for information exchange.
- Instead of reacting to events, defend them aggressively. Outlooks on developing vulnerabilities allow companies to respond firmly to risks long before they turn into a major problem.
- Exchange threat intelligence with industry groups. Many companies belong to Information Sharing and Analysis Centers (ISACs), where the news about both present and emerging risks is distributed.
- Businesses should check threat intelligence regularly in order to ensure that their protections are always updated. This covers techniques like running software updates, changing firewalls, and modifying IDS settings to find the latest attack paths.
Eventually
A good cybersecurity plan is majorly the result of threat intelligence research. Organizations can proactively defend, improve incident response, and strengthen general security posture by keeping updates on the most recent threats, vulnerabilities, and attack techniques.
Investing in threat intelligence can help companies stay ahead of cybercriminals and effectively safeguard their data, systems, and operations as these threats increasingly become complex.