Online Data Privacy: Protecting Your Digital Footprint in a Connected World
- “Data is the new oil.”
- — Clive Humby (Mathematician and Entrepreneur)
Hearing about data breaches is, unfortunately, not a rare occurrence anymore. Every year, millions of such incidents, resulting in the loss of billions of dollars, are reported. According to a recent report, the average cost of data breaches in 2024 was reported to be $4.88 million globally. (IBM: Cost of Data Breaches)
Such statistics raise various red flags, but all we can do about it is take the right precautions because one thing is certain in this highly interconnected world: playing fast and loose with your data will bring nothing but terrible outcomes.
Nevertheless, most people do not even know where to begin, especially when everything is so interconnected that individuals need to enter their sensitive financial details to make the smallest of purchases.
In this post, we will discuss effective techniques to help protect your data from being spied on or stolen. So, read on to learn more.

Use A Data Broker To Remove Your Data
Many people are not even aware of what a data broker service is and how it works. The first step to ensuring online safety from cyber criminals wanting to cause digital harm or simply harass people into performing an action (signing up for something or making a purchase, etc.) is to erase information from all the places that have paid for and harvested your data over the years.
Whenever you have done anything that involves even the most minute aspect of digital life, it is likely a company has bought that data to use in whatever way they choose. This could be benign or malicious, but the point is that neither is good.
This can be done by yourself, but it’s so incredibly time-consuming and, in some cases, complicated that no one can ever be 100% sure that they have sanitized themselves from the various databases around the world.
Fortunately, there are multiple tools to remove data that can be used to sift through the online world to find and eliminate it. These solutions save an inordinate amount of time, and because most work on a monthly or annual subscription basis, it will ensure that you remain as anonymous as possible without the need for constant input.
To put it out in simple words, it is a set-and-forget type of thing and will continue to scrub the data from the places you don’t want it to exist.
DO YOU KNOW? Nearly 68 records are compromised per second.
Opt For An Email Alias When Signing Up For Things
In most cases, the data in question is the email used for signing up and logging into things. Although many of us are far more savvy about how we use our email addresses compared to even only a decade ago, it’s still demanded for various actions.
Even using it for non-malicious activities like logging into software, etc., if that service gets hacked, the sensitive information in it will follow. As a solution, an alias address that connects to the real one can be used. This will give you control to even delete it if things get out of hand.
Another interesting benefit is that it enables people to see precisely what company has sold their data or if they have been hacked, but the spam is sent to the alias provided. This information will act as proof to report them to the existing agency and see them punished for their lack of security or flagrant abuse of data regulations.

Consider Investing In A VPN
Since VPN is used commonly, and by now, most people must be aware of what a VPN is, we won’t have to go into detail about what they are and how they work. However, if you don’t already have one, this might be the time to take the leap. The best part is that they are incredibly affordable, and the costs can be lowered further by opting for a multiyear subscription.
They work by concealing the user information and making it nearly impossible to intercept them as they navigate through the digital world. But it is important to still practice good data hygiene, while a VPN will do most of the heavy lifting.
DO YOU KNOW?
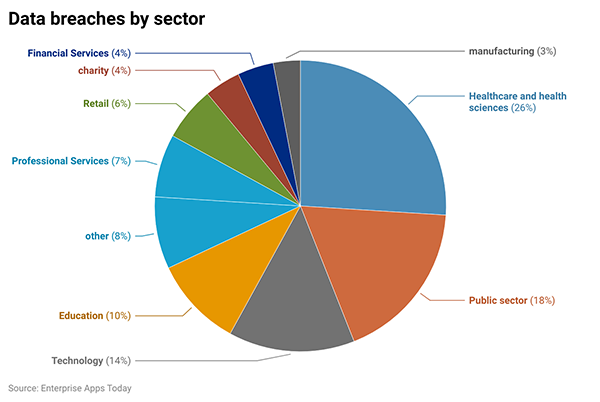
The healthcare sector is reported to be the most vulnerable industry to data breaches.
Always Use 2FA When Possible
Two-factor authentication has been around for a while now, and it continues to be a great way to keep attackers who have managed to figure out your password from going any further. Even though they aren’t as bullet-proof as many think, as with everything to do with security (both online and offline), the more roadblocks are put in the way, the more likely it is that a hacker will simply skip the hassle and look for an easier target.
When used in conjunction with a stone password, it allows you to rest assured, knowing that it is very unlikely to find yourself at the mercy of a cyber attacker.

Make Sure Your Passwords Are Secure (Or Use A Password Manager)
It might sound a bit odd to some, but the best password is one that even you can’t remember. The point is that if someone is able to memorize a password, chances are that it isn’t strong enough and will increase the chances of being attacked.
But if the password can’t be remembered, what will happen? Well, writing down on a piece of paper is out of the question, as is creating a plain text document on a phone or computer. The best possible choice is a password locker where all the various 12-14 character passwords can be stored, containing a mixture of letters, numbers, and symbols behind one strong password or passkey.
Those who have been in the tech world for some time might have heard of the LastPass hacks that profoundly dented the reputation of these services, but the fact remains that they are still the best option for the majority of people.
Maintaining online security is something that everyone knows they ought to do, but it isn’t something done all too well. The tips discussed in this article will help you get into a better position to scrub existing data from servers that aren’t used or needed anymore, and then remain safe as you go about the digital life.