Are Your Check Point VPNs Safe? Protect Against Network Breaches
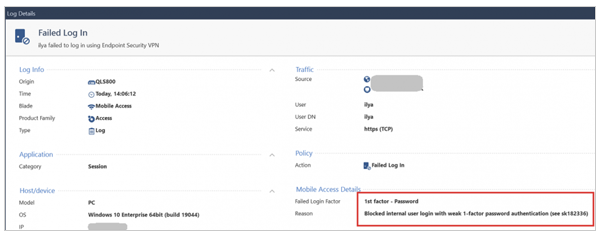
Hackers are targeting Check Point’s Remote Access VPN devices, trying to sneak into enterprise networks. Check Point sounded the alarm on Monday because these attackers are going after old local accounts with weak, password-only authentication.
They recommend using certificates with passwords to keep those hackers out.
Recently, Check Point noticed a few attempts to break into their VPNs using these outdated methods. By May 24, 2024, they had identified some login attempts with old accounts.
After a deeper look with their special teams, they found it wasn’t a massive wave but enough to spot a trend. The good news? There’s a straightforward way to block these attacks.
To protect yourselves, Check Point advises checking your Quantum Security Gateway, CloudGuard Network Security products, and any Mobile or Remote Access VPN software for vulnerable accounts.
Switch up your user authentication to something more secure (they’ve got a support doc for that) or just delete those risky accounts from the Security Management Server database. They’ve also rolled out a hotfix that stops local accounts with weak passwords from logging in at all. After you install it, those flimsy password-only accounts won’t be able to access the VPN.
For all the deets on beefing up your VPN’s security, Check Point’s got a support article with tips on handling unauthorized access attempts.
Check Point isn’t the only one in this VPN drama. Cisco recently warned that their VPN devices have been under attack too.
In April, Cisco flagged a wave of brute-force attacks on VPN and SSH services hitting devices from Cisco, Check Point, SonicWall, Fortinet, and Ubiquiti. These attacks started around March 18, 2024, using TOR exit nodes and other anonymizers to stay hidden.
In March, Cisco also noticed password-spraying attacks on their Secure Firewall devices running Remote Access VPN (RAVPN) services. These attacks seemed like early reconnaissance work.
Cybersleuth Aaron Martin linked this to a malware botnet called “Brutus,” controlling over 20,000 IP addresses from cloud services and home networks.
Last month, Cisco revealed a state-backed hacking group, UAT4356 (or STORM-1849), has been using zero-day vulnerabilities in Cisco ASA and Firepower Threat Defense (FTD) firewalls to hack government networks globally since at least November 2023. This cyber-espionage campaign is known as ArcaneDoor.