Email Security Protocols Every Business Should Implement
One of the most customary ways for businesses to communicate is emailing. Despite its reliability, emailing can be cybercriminals’ back door entrance for conducting exploits. For the prevention of such mishappenings, taking precautionary steps and implementing gateway email content filters, multi-factor authentication, and encrypting emails is of utmost significance.

It benefits businesses for a healthy cyber environment with self-reinforcing email authentication protocols, promoting protection against phishing and spoofing attacks, and in turn giving reduced spam emails.
In this article, we will get to know more about the different kinds of email security protocols, as well as how they work in providing and improving the cybersecurity for a business.
Encryption
Valuable data of the organization, confidential personal information – an email contains these and more, so it becomes a major issue if it falls into the wrong hands, leading to unimaginable collateral damage.
Encryption secures data on email by scrambling it in a fashion that becomes readable only by the intended recipient. In addition, it prevents hackers from intercepting the email, saving the data from being tampered with.
Email security protocols can allow encryption as well, such as S/MIME, providing end-to-end encryption by leveraging digital signatures for email authentication. This is rather a simple security measure benefiting the user by eliminating the multi-step process to secure attachment files.
Did You Know?
Julius Caesar used encryption in the days of the Roman Empire to cipher letters and messages.
Two-factor authentication (2FA)
Two-factor authentication (2FA) adds an extra step of verification along with the password. Based on the 2FA protocol being followed, the extra step can be either a knowledge factor (something a user knows) or a possession factor (something the user has).
2FA helps prevent network attacks by refusing the use of stolen login credentials, moreover preventing phishing attacks as it validates the user for being the legitimate owner or not trying to log in.
Implementation of 2FA is often demanding due to the high cost and assets involving hardware tokens, authentication apps, and training, creating the need for a balance between security and user experience.
End-to-End Encryption (E2EE)
End-to-end encryption works by converting a message into ciphertext before sending, and then the recipient uses their private key to decrypt the ciphertext back into its original form. Only after that the message can be read and modified.
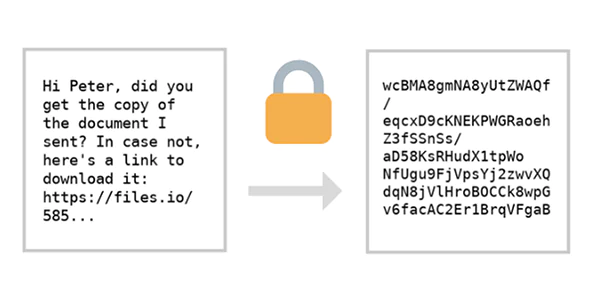
E2EE renders tampering with the encrypted message useless, as the altered message in transit will be easy to identify thanks to the ciphertext, and the altered message will no longer match with the ciphertext.
It also promotes privacy and aids in ensuring compliance with regulations governing the handling of sensitive data. Such an industry would be healthcare, requiring protection against unauthorized access and exploitation of patient data.
Secure Sockets Layer/Transport Layer Security (SSL/TLS)
Clients use secure sockets layer (SSL) and transport layer security (TLS) protocols for the sending and receiving of messages over the server, in addition, these protocols provide a layer of encryption.
The protocols ensure data is sent securely between the application and the server, preventing eavesdropping by third parties. They also digitally sign data to verify the identity of the sender. It is fundamental to protect against man-in-the-middle attacks and other potential attack vectors.
SSL/TLS is most familiar to users from Web browsing, where the padlock icon appears when a connection is encrypted. But it is also used in instant messaging, file transfers, video/audio conferencing applications, and email.
DomainKeys Identified Mail (DKIM)
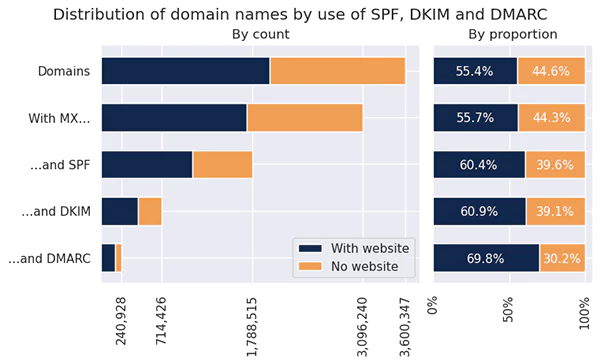
DomainKeys Identified Mail (DKIM) protects data by securing a digital signature to emails using a private and public cryptographic key. It uses cryptographic verification alongside SPF and DMARC to authenticate an email’s sender identity.
Its primary objective is safety against cybercriminals who spoof or tamper with emails sent on an organization’s behalf. It verifies that the email came from the organization. IPS can validate the DKIM signature by looking it up in the DNS TXT record as the signer’s public key.
Emails that use DKIM are more likely to reach their recipients’ inboxes and less likely to be filtered as spam or phishing attacks. Moreover, it allows recipients to verify that the email’s contents have not been tampered with in transition.
DKIM helps prevent the sender’s mail from ending as filtered spam or phishing attacks. However, it does not protect organizations from email spoofing, which occurs through the change of visible parts of the message header, such as the sender’s address and display name.
Message Authentication Reporting and Conformance (DMARC)
Fulfilling the gap left by DKIM, DMARC combined with SPF and DKIM averts email spoofing and phishing attacks by permitting domain owners to publish an authentication policy.
It instructs receiving mail servers on emails that don’t pass SPF or DKIM validation to take action, such as monitoring the email, quarantining it, or rejecting it. It is highly advisable to prioritize DMARC since it is a vital email security protocol for businesses.
As the DMARC record falls into place, domain owners can begin monitoring and analyzing aggregate reports from recipients’ mailboxes using AFRF or IODEF. The reports then become capable of identifying patterns in email spoofing, spamming, and phishing.
Conclusion
Email security is not guaranteed, and although the various email platforms do their best to prevent such issues, users can easily fall prey to cybercrime, fraud, and such. By following these email security protocols, the chances of getting business emails falling victim will be much slimmer since attackers will most likely prefer more vulnerable users.