The Cyberattack That Could Destroy Your Business Overnight—And How to Stop It
Jump To Key Section

Did you know? “Everyday, on average, 2,244 cyberattacks are officially reported. In which the most common attacks include malware, ransomware, and network beaches.”
Imagine yourself as a business owner, waking up one morning to find out your entire business has been shut down due to a cyberattack. This is not only imagination, but a harsh reality faced by many business people.
Cyberattacks are no longer like simple viruses, but deep operations run by a whole team of cybercriminals.
And it is not like that only big corporations are their target; small to medium-sized companies that have weaker defenses are hit by them.
Therefore, it is high time to get a cybersecurity solution shield installed for your reputation and overall business protection.
Before moving ahead, let’s dive into today’s topic: cyberattacks and their prevention techniques in this article.
Key Takeaways
- Cyberattacks are nowadays rising fast and can shut down your business overnight if you are not prepared.
- Ransomware is a major threat that locks your data and demands payments with no guarantee of recovery.
- If systems are outdated, then there are chances of security breaches, so taking regular security audits can fix this.
- Multi-layer authentication, firewalls, and regular data backups are essential for protection.
- Cyber resilience is a continuous practice of learning, adapting, and improving to protect a business.
The Rising Threat of Cyberattacks
As the technology is becoming accessible to everyone, the risk of cybercrimes is increasing. The cyberattackers are not limited to common people but are targeting businesses of all sizes.
Beyond that, these threat attackers are now using advanced tools and tactics, often supported by organized crime or state-funded groups. These thieves exploit software vulnerabilities, lead phishing campaigns, and disrupt systems.
Now, leaders need to stay updated on emerging trends and understand that cybersecurity protection is no longer an option but a necessity.
The One Attack That Could End It All
Although there is no single way, these attackers are choosing ransomware as the most devastating internet attack today. In this type of attack, malicious software encrypts an organization’s data, making it impossible to access unless a ransom is paid.
Beyond the financial loss, there is another huge downside: this attack completely shuts down business operations. Because there is no guarantee of regaining access to your data or preventing further exploitation even after paying.
How Vulnerable Is Your Business Right Now?
Many businesses overestimate their cybersecurity alertness, and the hybrid shift has also widened the surface attack. Corporations that lost their entity due to data privacy breaches are found to have the following issues.
- An outdated software.
- Unpatched system.
- Unsecured remote access.
A lack of investment in proper security may expose companies to attackers. For this, they need to conduct regular risk assessments and must activate the multifactor authentication (MFA) system.
Fun Fact
“Ninety five percent of data breaches are caused by human errors.”
Conducting Internal Cybersecurity Audits
Before conducting the internal cybersecurity audits, you must understand the types of cyberattacks and their process, depicted in the image below.
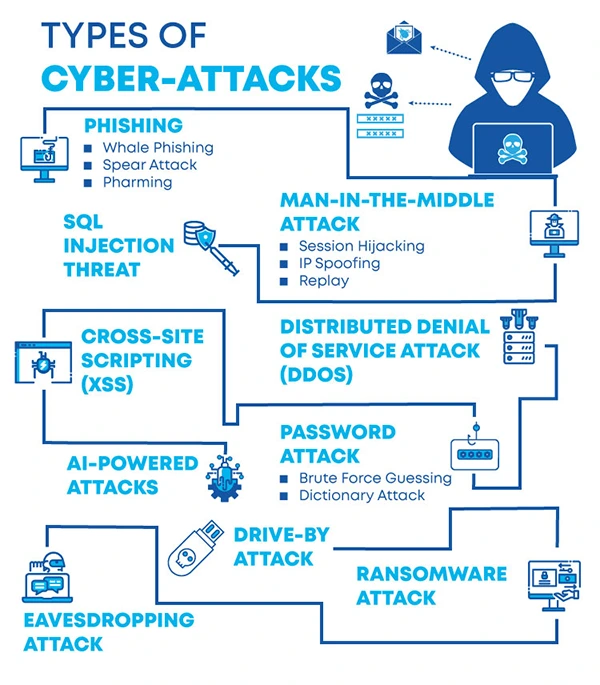
Afterward, you need to conduct a complete cybersecurity audit, which includes a policy, systems, and user behavior examination. It uncovers the weak points and compliance with data protection laws by reviewing every corner.
With the help of red teaming, you will get complete software security solutions. This approach goes beyond traditional audits by testing how well people, processes, or systems respond to a live attack.
Proactive Measures to Prevent a Cyberattack
There are multilayer security strategies required to prevent a cyber-attack. It begins with setting a strong password policy and enforcing multifactor authentication (MFA) to regularly eliminate unknown vulnerabilities.
You can use firewalls, point protection, and network segmentation to minimize access and isolate threats. Employee training should also be ongoing, as human error is a prominent cause of breaches.
Lastly, businesses must integrate cybersecurity into every company procedure to control the risk.
Building a Cyber-Resilient Culture
Technology alone cannot save your data from cyber criminals; your organization’s ultimate goal matters. This means a cyber-resilience culture starts with leadership. The process includes prioritizing security, allocating budget, and modelling good practices.
Whereas, regular awareness training, stitching simulation, and communication are other factors that build trust and accountability.
Thus, when everything is well-managed, your defense becomes stronger than any one tool.
What to Do If You’re Attacked
In case a cyberattack occurs, act quickly and with diligence, don’t panic. Follow these steps for safeguarding your business data
- Notify your IT and security team immediately.
- Document the attack in detail: what, how, and where it happened.
- Contact legal counsel and inform regulatory bodies or customers (if required).
- Avoid paying ransom; instead, rely on a clean backup and recovery process.
Always take the help of an expert, such as a cybersecurity firm, that can assist with forensics mitigation and recovery.
Final Thoughts
Cyberattacks are significantly increasing, which can impact businesses, and due to this, most of them are facing shutdowns overnight. Cybersecurity has become a business survival issue rather than just an issue.
From ransomware to phishing, threats are evolving faster than the speed of sound. Tomorrow might be too late, so just start building your cyber resilience today.
Frequently Asked Questions
Ans: Ransomware is currently one of the most common attacks on a business.
Ans: If a business stores sensitive data and lacks a strong cybersecurity protocol like multifactor authentication, it is likely at risk.
Ans: MFA is multifactor authentication, which adds an extra layer of protection by requiring users to verify their identity using a password and a phone code.
Ans: The IT team prominently controls cybersecurity issues in a company.